Abstract:
In an age marked by pervasive digital surveillance, the need for privacy phones has become imperative. This post delves into the reasons behind the growing demand for privacy phones, explores the process of setting up these devices, recommends optimal networks and phone models, highlights open-source software choices, and addresses the challenges of transitioning from conventional smartphones. Additionally, we will discuss essential privacy-focused applications and conclude with reflections on the trade-off between freedom and convenience, incorporating insights from Michael Bazzell's book Extreme Privacy.
1. Introduction: The Imperative of Privacy Phones
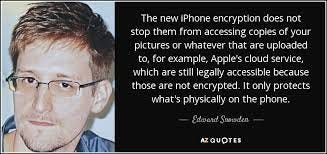
In an era where personal information is increasingly vulnerable to surveillance, privacy phones emerge as a crucial solution for individuals seeking to protect their digital autonomy. As Michael Bazzell notes in Extreme Privacy, "The more private information you expose, the more vulnerable you become." Edward Snowden’s revelation of the US government spying on its own citizens was a major catalyst for a focus on privacy:
If that wasn’t enough, Big Tech does its share of tracking, Google being worse, since it monetizes all your data rather than trying to make money selling phones and services as Apple does. Apple tends to be a little better on the privacy front and gives you more options to protect your privacy, but they still track plenty of your data as you’ll see below.
Google tracks various types of data on your phone, as the company provides a range of services and products that often involve the collection of user data. It's important to note that Google's data collection practices are outlined in its privacy policy, and users can manage their privacy settings to control what information is collected. Here's a detailed overview of the types of data that Google may track on your phone:
Location Data:
GPS Location: Google tracks your device's precise location using GPS data. This information is used for services like Google Maps, location-based search results, and location history.
Search and Browsing Data:
Search Queries: Google records the searches you perform, both through the Google search engine and voice searches using Google Assistant.
Browsing History: If you use Google Chrome, your browsing history may be synced with your Google account if you've enabled this feature.
Device Information:
Device Model: Information about your device, including the make and model.
Operating System: The version of the operating system your device is running.
Hardware Information: Details about the hardware components of your device.
App Usage Data:
Installed Apps: Google may collect data on the apps you have installed on your device.
App Usage Patterns: Information on how often you use specific apps and the duration of usage.
Google Services Interaction:
Gmail: If you use Gmail, Google collects data on your email communications and contacts.
Google Drive: Files stored on Google Drive may be subject to data collection.
Google Calendar: Calendar events and associated data may be tracked.
Google Photos: If you use Google Photos, your photos and videos may be analyzed for features like face recognition.
Ad-related Data:
Ad Interactions: Information about the ads you interact with, including clicks and views.
Ad Preferences: Data used to personalize advertisements based on your interests and online behavior.
Voice and Audio Data:
Voice Commands: If you use voice commands with Google Assistant, recordings of your voice may be stored to improve voice recognition.
User Preferences:
Settings and Preferences: Your preferences for various Google services, such as language preferences, customization settings, and personalized recommendations.
Sensor Data:
Sensor Information: Some Google services may use sensor data from your device, such as accelerometers and gyroscopes, to provide context-aware features.
Payment Information:
Google Pay: If you use Google Pay, your payment and transaction information may be stored.
Communication Data:
Call and SMS Data: If you use Google's Phone or Messages apps, information about your calls and text messages may be collected.
Apple places a strong emphasis on user privacy and has implemented various measures to limit the collection and tracking of user data. Apple's commitment to privacy is outlined in its privacy policy, and the company has introduced features like App Tracking Transparency to give users more control over how their data is used. Here's a detailed overview of the types of data that Apple may track on your iPhone:
Location Data:
GPS Location: Apple may collect location data for services such as Maps, Find My iPhone, and location-based suggestions. This data is often anonymized and used in aggregate to improve Apple's services.
Search and Browsing Data:
Safari Browsing Data: If you use Safari, Apple may collect data on your browsing activities. However, with features like Intelligent Tracking Prevention, Apple aims to prevent cross-site tracking.
Device Information:
Device Model: Information about your device, including the make and model.
Operating System: The version of iOS your device is running.
Hardware Information: Details about the hardware components of your device.
App Usage Data:
App Analytics: Developers can choose to integrate Apple's App Analytics to gain insights into how users interact with their apps. However, this data is aggregated and anonymized.
Apple Services Interaction:
iCloud: If you use iCloud services, data such as photos, videos, documents, and device backups may be stored on Apple's servers.
iMessage and FaceTime: Data related to your iMessage and FaceTime communications may be stored to facilitate message synchronization across devices.
Ad-related Data:
Apple Advertising: Apple uses on-device processing for personalized advertising, meaning that ad targeting is done on the device rather than on Apple's servers. Apple does not have access to the personal information used for ad targeting.
Health and Fitness Data:
Health App: If you use the Health app, Apple may collect and store health and fitness data. This data is often encrypted and can be stored securely on your device or in iCloud if you choose.
Voice and Audio Data:
Siri: If you use Siri, voice commands are processed on the device, and Apple retains anonymized voice recordings to improve Siri's performance. Users can choose to opt-out of Siri improvement in privacy settings.
User Preferences:
Settings and Preferences: Preferences for various system settings, customization options, and privacy settings are stored on your device.
Payment Information:
Apple Pay: If you use Apple Pay, payment information may be securely stored on your device through the Secure Element.
Communication Data:
Messages and Calls: Data related to your messages and calls may be stored on your device and synchronized across your Apple devices for continuity.
2. Setting Up a Privacy Phone: A Practical Guide
Setting up a privacy phone involves meticulous steps to fortify the device against potential privacy infringements. Users can either modify existing devices or opt for pre-configured models from reputable sources such as degoogled.it. Michael Bazzell emphasizes the importance of thorough preparation, stating, "Privacy is the result of meticulous planning and careful execution." Here are the basic steps if you are doing it yourself:
Choose a Privacy-Friendly Phone:
Select an Android phone with a good reputation for privacy. Consider models that are compatible with custom ROMs (e.g., LineageOS, GrapheneOS) for greater control over the operating system.
Install a Privacy-Focused Operating System:
Flash a privacy-focused custom ROM like LineageOS, GrapheneOS, or /e/OS on your device. This replaces the manufacturer's operating system with a more privacy-centric version.
Secure Your Lock Screen:
Set up a strong PIN, password, or pattern to secure your device. Avoid biometric authentication methods if possible for additional privacy.
Configure Device Encryption:
Enable device encryption to protect your data in case your phone is lost or stolen. This option is usually available in the security settings of your device.
Opt-Out of Data Collection:
Disable unnecessary data collection features, such as usage statistics, diagnostic data sharing, and personalized ads. Review and adjust privacy settings in the device's settings menu.
Use a Privacy-Focused Browser:
Install a privacy-centric browser like Firefox Focus, Brave, or DuckDuckGo Privacy Browser. Adjust browser settings to block trackers and cookies.
Set Up a VPN:
Use a reputable Virtual Private Network (VPN) to encrypt your internet traffic and enhance online privacy. Choose a VPN provider that prioritizes user privacy and does not log user data.
Install Privacy-Enhancing Apps:
Replace default apps with privacy-focused alternatives:
Messaging: Signal, Telegram
Email: ProtonMail, Tutanota
Search: DuckDuckGo
Maps: Maps.me, OsmAnd
Photo Storage: Nextcloud, Simple Gallery
Browser: Firefox, Brave
Manage App Permissions:
Review and adjust app permissions in your phone settings. Disable unnecessary permissions for apps that don't require certain access to function.
Secure Communication Apps:
Use end-to-end encrypted messaging and calling apps. Encourage your contacts to use these secure apps as well. Apps like Signal and Telegram offer strong encryption.
Secure Email Communication:
Set up a secure and private email account using services like ProtonMail or Tutanota. Ensure that email communication is end-to-end encrypted.
Limit Location Tracking:
Minimize location tracking by disabling location services for apps that don't require it. Use location-sharing sparingly and consider using a location spoofing app if needed.
Regularly Update Software:
Keep your device's operating system and apps up-to-date. Regular updates often include security patches that protect against vulnerabilities.
Back Up Securely:
Regularly back up your data using secure and private methods, such as encrypted cloud storage or local backups.
Educate Yourself:
Stay informed about privacy issues and best practices. Understand the privacy features of the apps and services you use.
3. Optimal Network Choices for Privacy Phones
Choosing the right mobile network is a critical aspect of ensuring privacy. While major carriers like T-Mobile, AT&T, and Verizon offer compatibility, the decision should consider each carrier's commitment to user privacy, but if you choose and configure the right phone the network shouldn’t matter as much. I have heard that privacy phones tend to work better on T-Mobile or AT&T networks and not so good on Verizon and you do need to check network compatibility with the phone you plan to use, which is a little easier if you are buying one already setup. As Bazzell highlights, "Privacy is not only about protecting your information but also about choosing services that respect your need for confidentiality."
4. Recommended Android Models for Privacy Phones
Android phones, with their open-source nature, present a viable option for privacy-conscious users. Notably, iPhones are excluded due to their proprietary software limitations. The main goal to enhance privacy is to disconnect the phone from “services” that typically run in the background of Android phones. This link can be severed with Android phones and they can still be used (with some diminished app functionality) pretty much as normal, but IOS phones cannot. Michael Bazzell underscores the significance of choice, stating, "Every decision in the world of privacy is about finding the balance between what works for you and what you are willing to sacrifice." Some good phones to consider are Purism Librem 5, Google Pixel 6 and Pine64 Pine Phone Pro. For more details, check out this article.
5. Open-Source Software for Privacy Phones
A range of open-source software options exists for privacy phones, each with its pros and cons. Choices such as Lineage OS, Graphene OS, Calyx OS and /e/OS provide users with customizable settings and enhanced security features. I have heard that Graphene OS is best for hard core privacy enthusiasts, but that loading and using apps can be a bit more of a challenge compared to for example, Lineage OS running MicroG. MicroG allows Android apps to access replica application programming interfaces (APIs) that are provided by Google Play Services, including the APIs associated with Google Play, Google Maps, and Google's geolocation and messaging features. It is important to note that as long as you are not signed into a Google account with MicroG, these server connections remain anonymous. The selection of an operating system should align with individual goals, reflecting Bazzell's insight that "true privacy is the result of smart choices, not just relying on technology."
6. Challenges in Transitioning to a Privacy Phone
Transitioning from a fully connected and surveilled phone to a privacy phone may pose challenges. Users accustomed to the conveniences of mainstream devices need to navigate a fairly significant learning curve, depending on the choice of phone and OS. If you are moving from IOS to Android, for example, that’s a unique challenge in itself, independent of the privacy element. It might be easiest to add a line to your phone plan and setup a separate privacy phone to start with, experimenting with the setup and different apps first before migrating everything over from your legacy phone. Bazzell acknowledges this difficulty, stating, "The transition to privacy is not always easy, but it is necessary."
7. Essential Privacy Apps for Critical Functions
Critical functions such as texting, email, search, maps, photo storage, and financial/banking can be safeguarded with privacy-focused apps. Signal, ProtonMail, DuckDuckGo, Maps.me, and using browser login vs apps for financial services exemplify choices that encrypt communications and data, aligning with Bazzell's assertion that "security comes from using the right tools for the job."
8. Freedom vs. Convenience: The Inevitable Trade-Off
The journey to privacy phones underscores the trade-off between freedom and convenience. While these devices offer enhanced security, users must be willing to sacrifice certain conveniences associated with mainstream smartphones. As Bazzell reflects, "Privacy is a luxury, and luxury requires sacrifice."
9. Conclusion: The Price of Digital Freedom
In conclusion, the pursuit of digital freedom through privacy phones necessitates informed choices and conscious sacrifices. Michael Bazzell's insights remind us that privacy is not an inherent right but a conscious effort. As we navigate the digital frontier, we must recognize that freedom isn't free; it demands vigilance, adaptation, and the willingness to make trade-offs in the name of securing our digital autonomy.
Not financial or legal advice, for entertainment only, do your own homework. I hope you find this post useful as you chart your personal financial course and Build a Bitcoin Fortress in 2023.
Thank you for supporting my work. Always remember: freedom, health and positivity!
Please also check out my Bitcoin Fortress Podcast on YouTube here and on all your favorite streaming platforms. I do a weekly Bitcoin news update every week on current items of interest to the Bitcoin community, usually 30 to 60 minutes depending on the number of topics to cover. Please check it out if you haven’t already. Also now on Fountain, where you can earn Bitcoin just for listening to your favorite podcasts.
Follow me on Nostr:
npub122fpu8lwu2eu2zfmrymcfed9tfgeray5quj78jm6zavj78phnqdsu3v4h5
If you’re looking for more great Bitcoin signal, check out friend of the show Pleb Underground here.
Lightning tips appreciated here.









i just recently sent in a pixel 7 pro to Mark37.com to ghost it. They were excellent and only charged me 250$ and they accepted crypto payments. excellent choice.